HTML Injection: The Silent Threat Lurking in Your Web App
Hey folks! Welcome back to my blog. Today, we’re diving into HTML injection, a sneaky vulnerability that can wreak havoc on web applications if left unchecked. Whether you’re a beginner or a seasoned developer, this post will break down HTML injection from the ground up, sprinkle in some technical goodies, and arm you with practical examples and prevention tips. Let’s dive in!
TL;DR
- HTML injection is a vulnerability where attackers inject malicious HTML code into a web page, potentially altering its appearance or behavior.
- It’s caused by improper input sanitization and can lead to defacement, phishing, or even XSS in severe cases.
- To prevent it, validate and sanitize user inputs, use secure coding practices, and employ tools like Content Security Policy (CSP). Below, we’ll explore this in detail with examples and recommendations.
What is HTML Injection?
Imagine you’re running a blog like mine, and you allow users to post comments. One cheeky user submits a comment with some HTML tags, like <b>Bold text!</b>. If your site doesn’t properly handle this input, that HTML could render as Bold text! in the comment section. That’s HTML injection in a nutshell—attackers sneaking HTML code into your site to mess with its look or functionality.
Unlike its cousin, Cross-Site Scripting (XSS), HTML injection doesn’t always involve JavaScript. It’s about injecting HTML elements that the browser renders. However, if attackers escalate it with <script> tags, it can become XSS. Think of HTML injection as a gateway to bigger problems if not addressed.
Why Does It Happen?
HTML injection occurs when:
- User inputs (like forms or URL parameters) aren’t properly sanitized or escaped.
- The server blindly renders user-supplied data as HTML.
- Developers trust user inputs too much (never do this!).
For example, a poorly coded comment section might take a user’s input like <h1>Hacked!</h1> and display it as a giant heading on your site. Not cool, right?
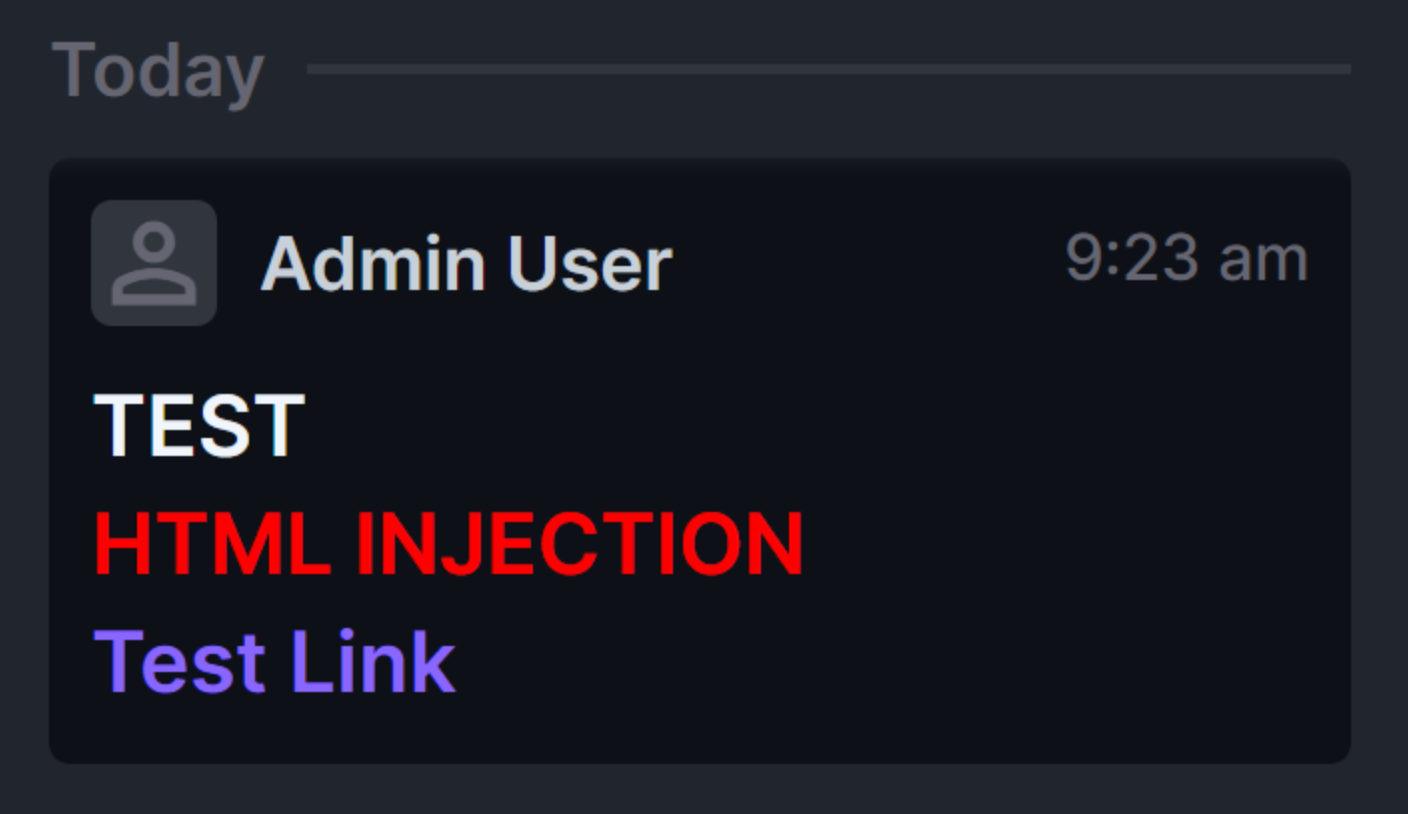
PATCH /activity/comment/3 HTTP/2
Host: directus.local
{
"comment": "<h1>TEST <p style=\"color:red\">HTML INJECTION</p> <a href=\"//evil.com\">Test Link</a></h1>"
}
Deep Technical Dive into HTML Injection
Now, let’s get our hands dirty with the technical stuff. HTML injection exploits the way browsers parse and render HTML. When a web application accepts user input and includes it in the page’s HTML without proper escaping, the browser treats it as legitimate markup.
How It Works Under the Hood
- User Input: An attacker submits malicious HTML via a form, URL parameter, or other input field.
- Server Processing: The server stores or reflects the input without sanitizing it.
- Browser Rendering: The browser receives the page, parses the injected HTML, and renders it, altering the page’s structure or behavior.
For instance, consider a vulnerable PHP script:
<?php
$comment = $_POST['comment'];
echo "<div>$comment</div>";
?>If an attacker submits <img src="invalid" onerror="alert('Hacked!')">, the browser might execute the onerrorJavaScript, turning this into XSS. This is why HTML injection can be a stepping stone to more dangerous attacks.
Types of HTML Injection
- Stored HTML Injection: The injected HTML is saved (e.g., in a database) and displayed to all users, like in a comment section.
- Reflected HTML Injection: The injected HTML is reflected back in the response, affecting only the user who triggered it (e.g., via a manipulated URL).
- DOM-Based HTML Injection: The injection happens client-side, manipulating the DOM directly (less common but still dangerous).
Risks and Impact
- UI Defacement: Attackers can change how your site looks, scaring users or damaging your brand.
- Phishing: Injected forms can trick users into submitting sensitive data.
- Escalation to XSS: If JavaScript is allowed, it becomes full-blown XSS, potentially stealing cookies or session tokens.
- Data Leakage: Injected
iframesor redirects can send users to malicious sites.
Recommendations to Prevent HTML Injection
Preventing HTML injection is all about secure coding and vigilance. Here are actionable tips:
- Sanitize Inputs:
- Use libraries like DOMPurify (JavaScript) or bleach (Python) to strip malicious HTML.
- Escape special characters (e.g.,
<to<) before rendering.
- Validate Inputs:
- Define strict rules for acceptable input (e.g., only alphanumeric characters for usernames).
- Reject or strip HTML tags unless explicitly needed.
- Use Safe Frameworks:
- Frameworks like React or Angular automatically escape outputs, reducing risks.
- Avoid direct DOM manipulation with unsanitized data (e.g.,
innerHTML).
- Implement Content Security Policy (CSP):
- Add a CSP header to restrict which scripts can run, mitigating XSS escalation.
- Educate Your Team:
- Train developers on secure coding practices and the dangers of trusting user inputs.
References
For further reading, check out these awesome resources:
Wrapping Up
HTML injection might seem like a small fry compared to heavyweights like XSS or SQL injection, but it’s a real threat that can tarnish your site’s reputation or lead to bigger attacks. By understanding how it works, testing your apps, and following secure coding practices, you can keep the HTML Injection Monster at bay.
Stay secure, folks, and I’ll catch you in the next post.




